|
|
|
Windows Server 2003 defines a universe of system administration responsibilities. Yet only a few system administrators have the broad enterprise-level view. Instead, they have specialized responsibility for planning and deployment of such things as domain controller servers, domain models, the Active Directory, sites, security policies, and network infrastructures.
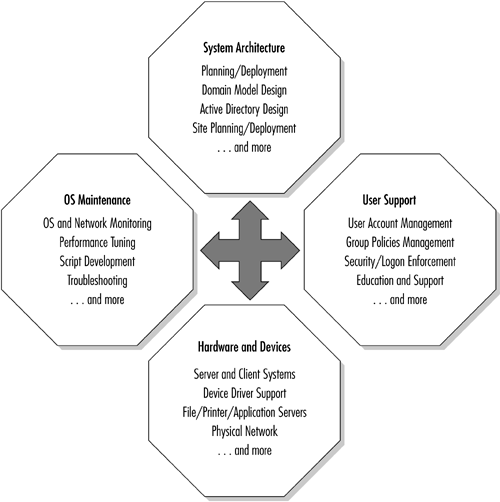
Because the majority of administrators perform these more specialized functions, Windows Server 2003 allows the assignment and delegation of both broad and function-specific roles (Figure 1.2). An administrator could have all or a portion of these management responsibilities:
Operating system maintenance— the health of the operating system's processes and services. The monitoring and logging tools help tune individual computers, domain controllers, and specialized server performance. In this work, many administrators find both standard tools and custom scripts handy.
User and group management— adding, modifying, and deleting user accounts and group policies. Windows Server 2003 security groups are used to establish the rights and privileges of individuals and groups of users. Underlying group policies are the establishment and enforcement of security and user behavior. The Active Directory services manage the distribution of group policies. This includes such activities as logon and password management, and granting or restricting permissions and access.
Hardware and device management— the health of the physical network devices, computers, and peripherals. Microsoft provides a Hardware Compatibility List (HCL) to assess the viability of a given item of hardware in a Windows environment. This also permits the system administrator to ensure that the most recent device drivers for the hardware components are being used. This involves not only traditional network hardwired connections but also such items as wireless devices and assessment of Internet and intranet bandwidth.
Windows Server 2003 provides for levels of administrative authority, for which there exists a relative hierarchy. An administrator gains authority by becoming a member of one or more built-in or default security groups, inheriting the rights, privileges, and restrictions associated with each (Figure 1.3). In Chapter 7 we explore group policies in depth. However, for the sake of this discussion of administrative roles, we note that responsibilities are assigned through the accumulation of group memberships.

Another important concept is specialized function versus broad responsibility. Members of different groups have broad-based authority to manage domain activities. These include Administrators, Domain Admins, and Enterprise Admins. The scope of authority can be granted to other users with specialized functions—for example, printer support or backup operations. The specialized security groups are Account Operators, Backup Operators, Printer Operators, Replicators, and System Operators. Membership in these groups can be assigned individually or in any combination.
The final major concept is granularity. The organizational unit (OU) is a structural mechanism (also viewed as a container object) by which domains can be divided into smaller elements such as a sales department. In turn, this OU can be divided into other units that involve users, devices such as printers, and network components. Each parent and child OU can then be assigned specific system administrators to manage the allotted functions.
|
|
| Top |